As businesses embrace digital transformation, the cybersecurity landscape grows increasingly complex. Understanding the most common cyber threats is no longer optional—it’s essential. Companies must proactively identify and mitigate risks to safeguard sensitive data, maintain customer trust, and ensure business continuity.
Explore our complete cybersecurity solutions here.
Why Businesses Are Prime Targets for Cyber Threats
Growing Attack Surface
With the adoption of cloud computing, IoT devices, and remote work, the number of access points for attackers has skyrocketed.
Valuable Data
Businesses store customer information, financial records, and intellectual property—all prime targets for cybercriminals.
Lack of Awareness
Many small and mid-sized companies underestimate their vulnerability, making them easy prey for opportunistic attacks.
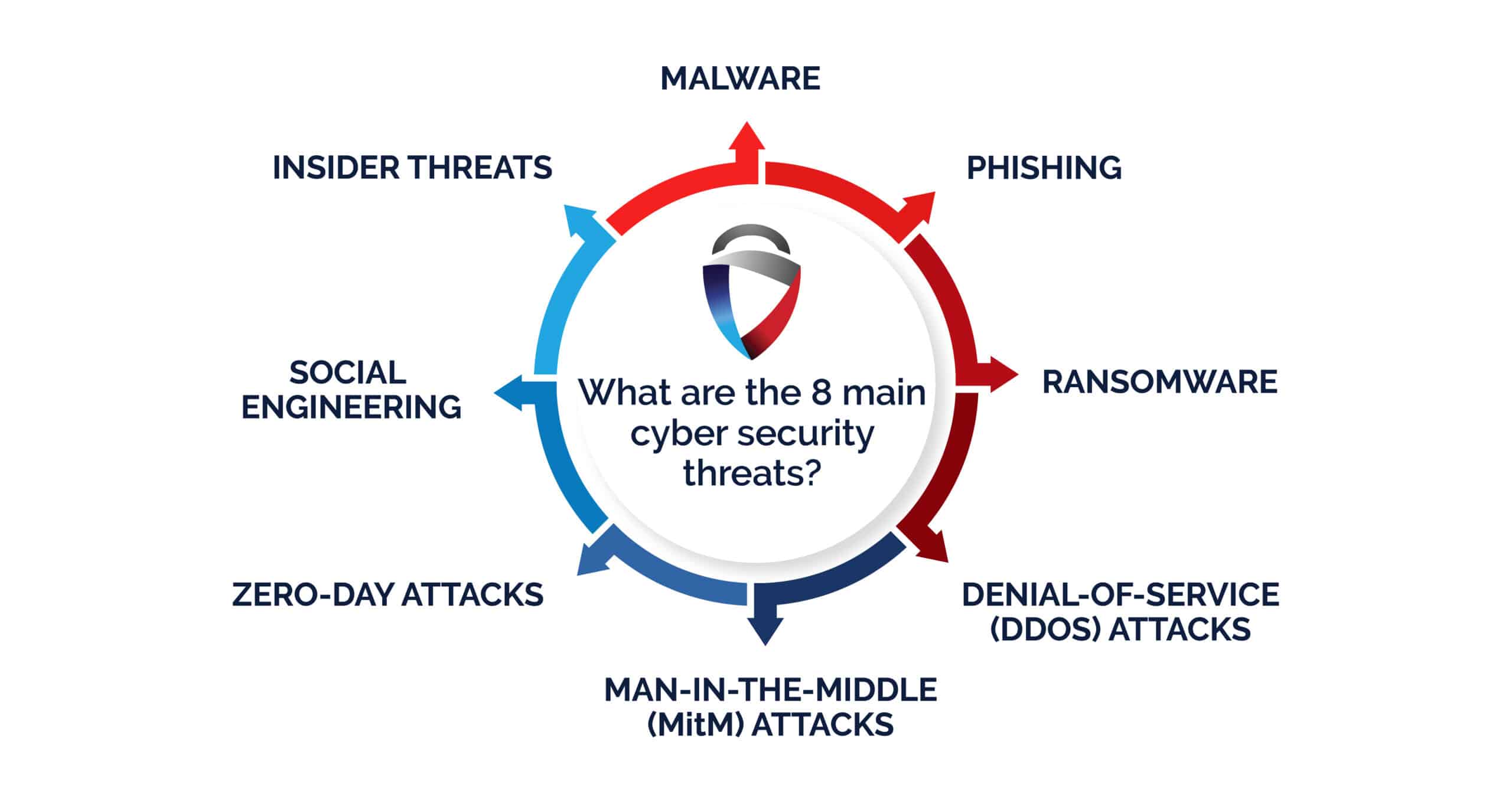
Top Cyber Threats Businesses Face in 2025
1. Phishing Attacks
Phishing remains the most common cyber threat. Attackers trick employees into clicking malicious links or sharing credentials through deceptive emails and messages.
2. Ransomware
Ransomware attacks encrypt company data and demand payment for its release. In 2025, ransomware has evolved to target backup systems, making recovery even more difficult.
3. Insider Threats
Whether intentional or accidental, insider actions can lead to serious data breaches. This includes negligent employees or disgruntled staff with access to sensitive systems.
4. Business Email Compromise (BEC)
Cybercriminals impersonate executives or partners to trick finance teams into making unauthorized payments.
5. Zero-Day Exploits
These are vulnerabilities that are unknown to software vendors and can be exploited before a fix is issued. Businesses must stay updated with patches and threat intelligence.
6. DDoS Attacks
Distributed Denial-of-Service attacks flood servers with traffic, disrupting business operations and damaging customer experience.
The Financial and Reputational Cost of Cyber Threats
Cyber incidents can cost businesses millions in lost revenue, legal fees, and regulatory fines. But perhaps more damaging is the loss of customer trust—a critical asset in the digital age.
Proactive Measures to Strengthen Cybersecurity
Conduct Regular Risk Assessments
Understanding where vulnerabilities exist is the first step to securing your infrastructure.
Implement Strong Access Controls
Use multi-factor authentication (MFA), strong password policies, and least-privilege principles.
Employee Training
Educating staff on identifying phishing attempts and practicing secure behavior is vital.
Work with Cybersecurity Experts
Partnering with experienced IT security providers like Singleclic ensures end-to-end protection.
The Role of Singleclic in Securing Your Business
Singleclic has been a trusted IT solutions provider since 2013, delivering comprehensive cybersecurity services across the Arab world. Our services include:
- Tailored cybersecurity strategies
- 24/7 technical support
- Secure cloud hosting and infrastructure
- Integrated threat detection and prevention systems
📞 Contact us:
Egypt: +2 010 259 99225
UAE: +971 42 475421
KSA: +966 58 1106563
🌐 Visit our website
People Also Ask
- What are the most common cyber threats businesses face today?
- What are the top 5 major threats to cybersecurity?
- What is the most common type of cyber threat?
- What are the 12 most common types of cyber attacks?
- What are the 5 C’s of cyber security?
- What is the role of cybersecurity in protecting personal data?
- What is cyber security and protection?
- What is protected data in cyber security?