Introduction
In today’s digital landscape, building a secure IT infrastructure is no longer optional — it’s a strategic necessity. For businesses operating in an era of constant cyber threats, a resilient infrastructure protects critical assets, ensures business continuity, and maintains customer trust.
As a leading IT solutions provider in the Arab world since 2013, Singleclic specializes in developing secure and scalable IT infrastructures tailored to diverse industries. Here’s your complete guide to building a secure IT ecosystem from the ground up.
Why Secure IT Infrastructure Matters
The Rise of Cyber Threats
Cyberattacks have become more frequent and sophisticated, targeting businesses of all sizes. From ransomware to phishing and zero-day exploits, attackers exploit weaknesses in networks, endpoints, and human behavior.
Business Impact of Security Breaches
A single breach can result in:
- Financial loss
- Reputation damage
- Legal liabilities
- Loss of customer data
Protecting your IT infrastructure is not just an IT concern — it’s a business survival strategy.
Key Components of a Secure IT Infrastructure
1. Network Security
Secure your LAN, WAN, and cloud environments with:
- Firewalls
- Intrusion Detection & Prevention Systems (IDS/IPS)
- Secure VPN access
2. Endpoint Protection
Protect every connected device (servers, workstations, mobile):
- Antivirus & Anti-malware
- Device encryption
- Mobile Device Management (MDM)
3. Identity & Access Management (IAM)
Ensure only the right people access the right resources:
- Multi-Factor Authentication (MFA)
- Role-based access control
- Single Sign-On (SSO)
4. Data Protection & Backup
- Regular encrypted backups
- Data Loss Prevention (DLP)
- Disaster Recovery Plans
5. Cloud Security
As cloud usage grows, so do its risks:
- Use secure cloud platforms (AWS, Azure, GCP)
- Enable encryption at rest and in transit
- Monitor for misconfigurations
Best Practices for Building Secure Infrastructure
Conduct Regular Risk Assessments
Identify vulnerabilities in your systems and applications.
Keep Systems Updated
Patch operating systems, apps, and firmware regularly.
Train Your Employees
Your employees are the first line of defense. Provide cybersecurity awareness training to prevent social engineering attacks.
Implement Zero Trust Architecture
Never trust, always verify — every access request should be authenticated, authorized, and encrypted.
Monitor & Respond in Real-Time
Set up SIEM (Security Information and Event Management) systems to detect anomalies and respond instantly.
How Singleclic Helps You Build a Secure IT Ecosystem
Since 2013, Singleclic has been delivering secure IT environments through:
- Custom software development (Low-code, ERP, CRM)
- Professional network design & infrastructure
- End-to-end cybersecurity services
- Hosting & cloud-native application support
- 24/7 technical support across the MENA region
📞 Contact us at:
Egypt: +2 010 259 99225
UAE: +971 42 475421
KSA: +966 58 1106563
🔗 Visit our cybersecurity page:
Cybersecurity and Data Protection
People Also Ask (FAQs)
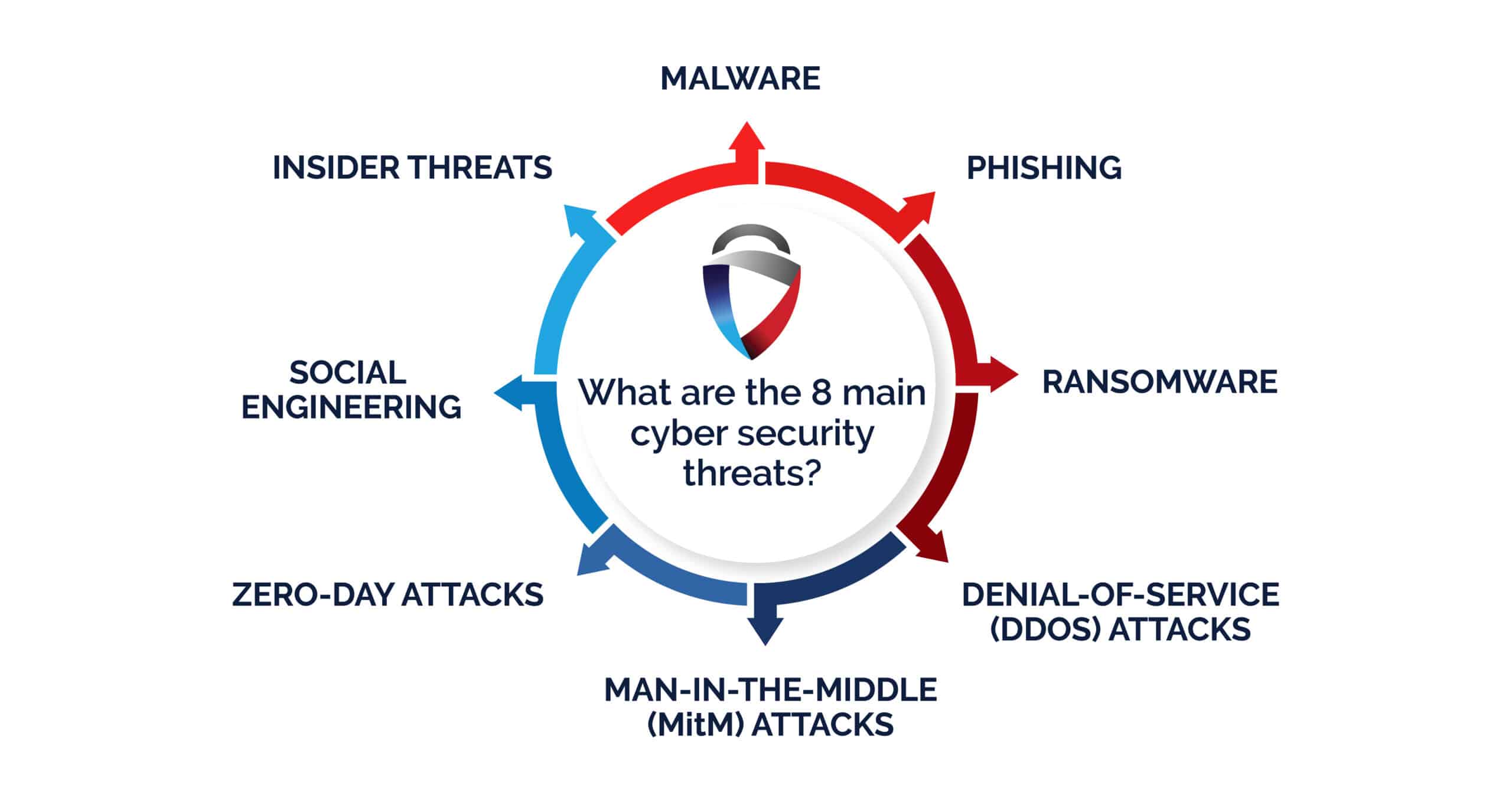
What are the most common cyber threats businesses face today?
Common threats include phishing, ransomware, insider threats, DDoS attacks, and zero-day exploits.
What are the 7 components of IT infrastructure?
They include hardware, software, networking, data centers, cloud services, cybersecurity, and support personnel.
How to secure IT infrastructure?
Apply layered security, use encryption, restrict access, regularly update systems, and train employees.
How to design a secure network infrastructure?
Use segmented networks, firewalls, IDS/IPS, VPNs, and apply least-privilege access policies.
Conclusion
Building a secure IT infrastructure is a proactive process — not a one-time task. By integrating advanced technologies with best practices, and partnering with experts like Singleclic, your organization can thrive in a digital world full of threats.
Whether you’re starting from scratch or upgrading your current setup, investing in security today ensures resilience tomorrow.